In the digital age, ensuring the integrity and authenticity of software is crucial to maintaining a secure computing environment. One essential method for verifying the legitimacy of software is by checking its digital signature. Software signatures provide an assurance that the software has not been tampered with and originates from a trusted source. In this blog post, we will delve into the process of verifying software signatures step by step, enabling you to make informed decisions about the software you install.
Understanding Digital Signatures
A digital signature is a cryptographic technique that associates a unique identifier with a piece of software, ensuring its integrity and origin. The process involves using a private key to create the signature and a corresponding public key to verify it. When software is signed, it attests that the software has not been altered since it was signed by the original developer.
Obtaining the Software
Before verifying a software signature, it is essential to obtain the software from a trusted source. Official websites, app stores, or reputable software repositories are the best places to download software. Avoid downloading from unfamiliar sources or third-party websites, as they may distribute tampered or malicious software.
Check for Digital Signatures
Once you have downloaded the software, navigate to the folder where the file is stored. Right-click on the file and select "Properties" or "Get Info" to access its properties or information. Look for a "Digital Signatures" tab or a similar option, depending on your operating system. This tab displays information related to the software's digital signature, including the signer's name and the signing status.
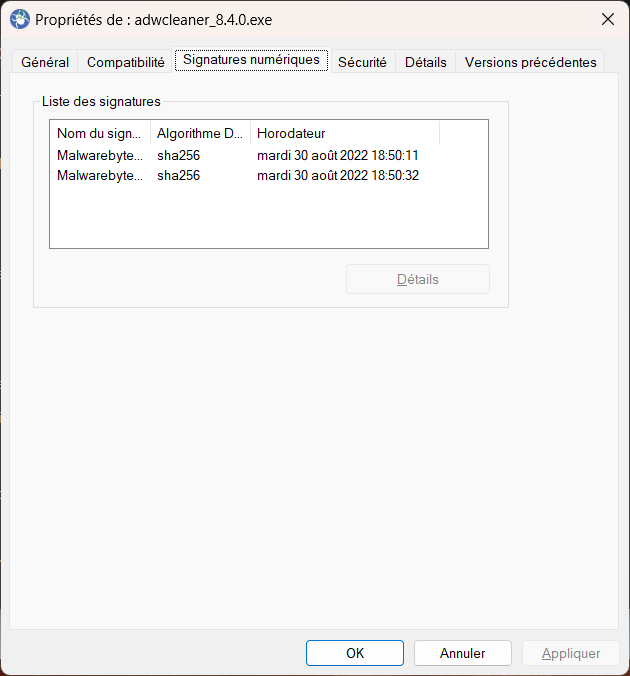
Verify the Certificate
Within the digital signatures section, you will find information about the certificate used to sign the software. Click on the signature and select the "Details" or "Certificate" button to view additional information. Ensure that the certificate belongs to the software developer or the organization responsible for distributing the software. Verify the certificate's validity by checking the certificate's expiration date and verifying that it has not been revoked.
Cross-Check Certificate Information
To ensure that the certificate is legitimate, cross-check the provided information with the software developer's official website. Look for a dedicated page that outlines their signing process, including details about the certificate authorities they use. If the information matches, you can be more confident in the software's authenticity.
Verify the Signature's Status
Within the certificate details, check the signature's status to confirm that it is valid. The signature should indicate that it is "valid" or "trusted." If the signature is "invalid" or "untrusted," exercise caution before proceeding with the installation. An invalid signature might indicate tampering or an issue with the signing process.
Perform a Hash Check
In addition to verifying the digital signature, you can perform a hash check on the software file. A hash check involves generating a unique cryptographic hash (such as MD5, SHA-1, or SHA-256) from the downloaded file and comparing it to the hash value provided by the software developer. If the hash values match, it ensures that the downloaded file is identical to the one the developer intended to distribute.
Utilize Trusted Software Tools
To simplify the process of verifying software signatures, various software tools are available. These tools can automate the verification process, ensuring that you can quickly assess the legitimacy of software. Some popular tools include Microsoft's Sigcheck, Gpg4win, or Kleopatra for Windows, and GnuPG or Keybase for cross-platform usage.
Verifying software signatures is an essential step in maintaining a secure computing environment. By following the steps outlined in this guide, you can ensure that the software you install is authentic and has not been tampered with. Remember to download software from trusted sources, check the digital signature and certificate details, and cross-verify information with the software developer's official website. Performing these checks will significantly reduce the risk of installing malicious or compromised software, enhancing your overall digital security.